A lot of fleet leaders can remember a time when uptime was all about keeping engines, tires, and brakes maintained well enough to get from Point A to Point B consistently. Then came ECUs and aftertreatment systems, telematics, and now even Artifical Intelligence. These technologies led to better performance and fewer emissions, but adding technology to trucks has also made them more vulnerable to the evolving class of digital highwaymen and cybercriminals planning to hold you up. You might think your fleet isn't big enough to draw their attention, but in the wild, predators rarely go after the biggest prey; they simply exploit the most vulnerable.
Mark Murrell, CarriersEdge president, said the posture some fleets have today toward cyber risk and cybersecurity is: “It’s not going to happen to me,” and it’s “computer stuff—I’m not a computer guy.”
But fleets with that position are setting themselves up for a cyberattack.
Last September, Estes Express Lines found this out the hard way when the fleet fell victim to a ransomware attack that blocked user access to their data or systems until a ransom was paid. Estes truck drivers were unable to electronically log their hours of service. While the company hired an external cybersecurity team, the ransomware attack took three weeks to resolve. According to the Maine Attorney General’s Office where the data breach notification was filed, the incident impacted more than 21,000 individuals. And that was just one incident.
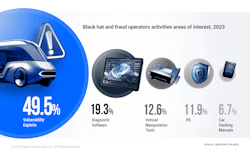
A report compiled by Upstream shows that cloud-based cybersecurity for connected vehicles grew significantly in 2023 from 2022. According to the report, server-related cyber incidents rose from 35% in 2022 to 43% in 2023, while infotainment-related incidents grew from 8% in 2022 to 15% in 2023.
“What we saw this year represents not a gradual but a dramatic inflection point in how cybersecurity is experienced in the industry,” said Shira Sarid-Hausirer, VP of marketing at Upstream.
Fleet companies would be wise to roll out more effective means of cybersecurity protection, beginning with proactive measures.
Both large and small trucking companies are targets of bad actors looking to exploit others for financial gain, and having fleets recognize that is a challenge, Murrell said.
“Trucking may not be a high-margin industry, but ... there's a lot of money going back and forth there,” Murrell explained. “When a hacker gets access to the network and starts looking at these numbers, they can initiate a ransomware attack that actually hits the company for a good amount of money, and they can do pretty well with that, even at a relatively small fleet. So, the industry, to take it seriously, needs to pay attention."
One way to guard a fleet from a cyberattack is to employ preventive measures—and staff training is the most critical aspect of that, Murrell told Fleet Maintenance sibling publication, FleetOwner. CarriersEdge developed a training course for all employees who work within a trucking company, from drivers to office personnel, to educate them on “what to watch for so they don’t fall victim.”
Another proactive step to reduce cyberattack risk is to employ safeguards and third parties to monitor risk.
Companies such as ProCircular, a cybersecurity company currently working with the transportation and logistics industry, and Upstream monitor systems and networks around the clock. Through both companies’ security operations centers, Upstream and ProCircular can immediately identify risks and work to resolve them. While this might look like a reactive measure, fleets that employ cybersecurity companies ahead of a cyberattack will have a resolution team in place when a cyberattack occurs.
Being proactive not only helps ward off threats but also “enables organizations to anticipate and identify gaps that cybercriminals may exploit to infiltrate their network through vulnerabilities or other weaknesses in systems,” said Brandon Potter, CTO of ProCircular. Once these gaps are identified, companies can address them appropriately.
ProCircular helps fleets shorten these gaps through its Virtual Chief Information Security Officer program that “helps organizations establish a holistic cyber resilience program that is integrated throughout the organization,” Potter told FleetOwner.
See also: What fleets should know about growing threat of cyberattacks
Cyberattack response
The rise of cyberattacks on vehicles and fleets from 2022 to 2023 alone is enough to elicit a proactive response from fleet owners, but Sarid-Hausirer said hackers and “bad actors” are continually educating themselves and searching for vulnerabilities in businesses. This places unprotected fleets at a high risk for a cyberattack, but it also means even protected fleets might find themselves victims of an attack. When this happens, it’s essential to act quickly.
Fleets that employ companies like ProCircular and Upstream will have the biggest advantage because anomalies and risks are detected more quickly with close monitoring. Fleets that don’t employ round-the-clock monitoring might have a hacker in their system for days before it becomes known. Potter said that about 20% of ProCircular’s workload is reactive and handles the “eviction” of a hacker from a client’s network as quickly as possible.
“We use forensic artifacts and analyze the facts to answer the important questions of ‘what, when, how, and why’ to understand the scope of the incident,” Potter said of ProCircular’s cyber incident response. “Doing so also helps fleet owners make informed decisions to mitigate the impact and prevent similar incidents in the future.”
On the other hand, while Sarid-Hausirer described Upstream as a “detection response platform,” it monitors connectivity that’s specific to vehicles. It covers vehicle security in a three-layer approach: vehicle data monitoring, cloud data monitoring, and vehicle application monitoring. This three-layer monitoring offers a “holistic approach to protecting the [connected vehicle] ecosystem,” she said.
If Upstream detects a threat, the team will take immediate action, allowing organizations to respond to the threat seamlessly.
Fortify your fleet
The need to protect a fleet and transportation business from a cyberattack might seem obvious, but the scale and monetary impact make it imperative.
Upstream’s 2024 Global Automotive Cybersecurity Report referenced a $70 million ransomware attack on a semiconductor manufacturer in Taiwan that occurred in June 2023. In November 2023, the same ransomware group attacked an Australian automotive group and stole 50 GB of sensitive data, including payroll information, payout information, invoices, and more. The files were published after the ransom deadline expired, Upstream reported.
A $70 million ransom demand can cripple a business, but the theft and publishing of sensitive information can also inflict extensive damage to a company’s reputation and customers’ trust in that company.
All fleets are at risk, even those with few “connected” vehicles. Through simple practices, a hacker can infiltrate a company by sending an email with a suspicious link to an employee. If these hackers can access a staff member’s account information, their reach within sensitive company activity could be vast.
“Once you have access to somebody's email, you can create a lot of havoc,” Murrell said. He said simple login credentials could provide a hacker with access to information such as the fleet’s network data, payroll systems, and more.
While every fleet is at risk, the more connected fleets are the most vulnerable. This connectivity includes data gathered from telematics systems, ELDs, and even a vehicle’s infotainment system. As vehicles become even more connected through the implementation of EVs, EV chargers, telematic system integrations, and more, the threat only becomes larger.
“With ever-increasing reliance on connected technologies and the uptick in digital footprints, fleet managers and owners are expanding their attack surface daily, potentially making their organizations more vulnerable,” Potter told FleetOwner.
Every employee plays a role in keeping the company safe from cyberattacks, and it’s also essential for leadership and decision-makers to employ a safeguarding system within their network. CarriersEdge’s cyber training course can help employees—including drivers—identify risks, while implementing a third-party monitoring team, like Upstream and ProCircular, can help protect fleets on the back end, whether that’s monitoring the connected vehicle or the fleet’s internal network.
“To the fleet reading this, you are being targeted today,” Murrell said. “Please take it seriously.”
This article originally appeared on FleetOwner.com.
About the Author

Jade Brasher
Senior Editor Jade Brasher has covered vocational trucking and fleets for the past five years. A graduate of The University of Alabama with a degree in journalism, Jade enjoys telling stories about the people behind the wheel and the intricate processes of the ever-evolving trucking industry.